What is a DDoS?
What is a DDoS, Really?
With all the talk about cyber attacks, cyber terrorists general security across the internet, I thought I’d take a few moments offer some insight into one of the least understood and most prevalent cyber threats on the web, the DDoS.
What is a DDoS anyway?
Well I’m happy you asked! A Distributed Denial of Service (DDoS) attack is exactly that: An attack, sourced from a distributed network, whose aim is to deny responses from your services. Simply put, someone is trying to take up all your server’s resources with nonsense requests which renders your server unable to respond to legitimate clients.
How do they work?
Well! Most DDoS attacks can be broken down into to basic classes: Volumetric or Service-Level.
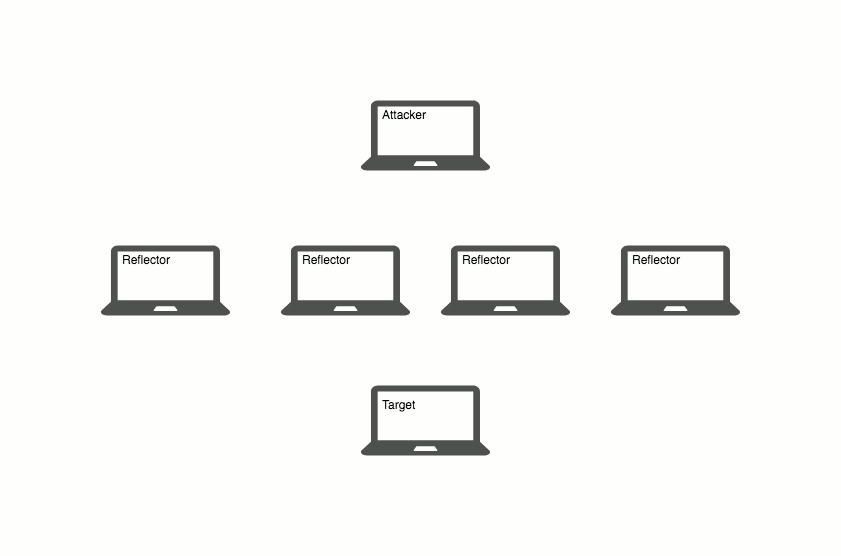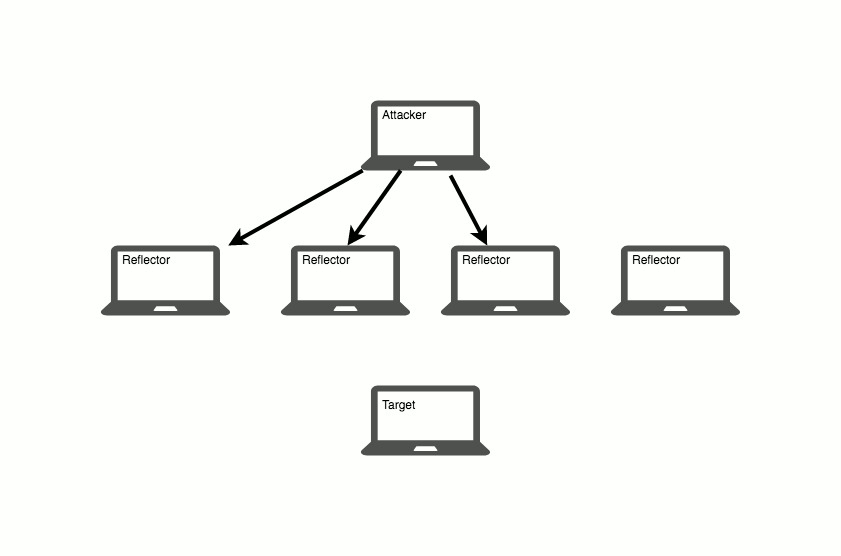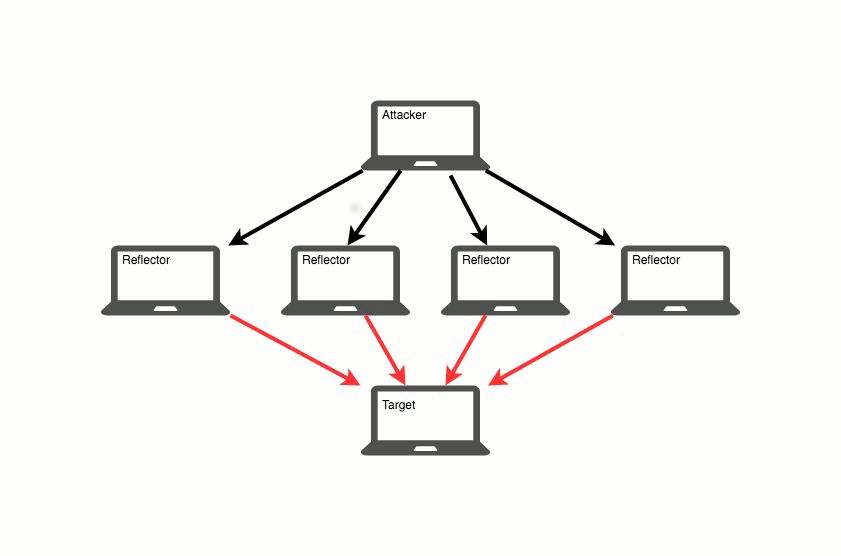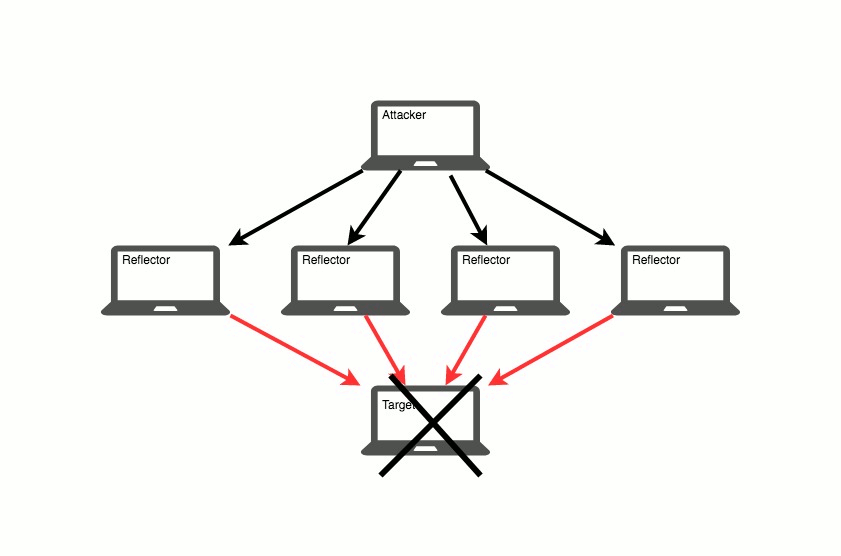
Volumetric DDoS attacks, which include things like Flooding and Reflection, are the less sophisticated and more frequent of the two. The process is simple. An attacker, usually hidden by sourcing from thousands of IP addresses, will send traffic in such large quantities that it inundates the server’s connection. While the connection is clogged, the server doesn’t receive traffic from real clients and service is denied.
Service-Level attacks, often called SYN floods or SYN Attacks, are more sophisticated and require actually reaching the server with a legitimate request. This request, called a SYN (pronounced sin), opens a connection to the server and the server responds with an acknowledgment called an ACK (pronounced ack). So far so good. The problem arises when the attacker continues to send these SYN packets to the server with no intention of actually completing their request. Services have a finite number of connections that can be open at once. Once that number is depleted, new connections cannot be established and service is denied.
But I’m safe, right?
Mostly. Liquid Web employs a two-fold mitigation platform which can mitigate most attacks seamlessly. Our first line of defense, an always-on solution situated at the edge of our network, is designed to handle just about any volumetric attack. This first step is constantly inspecting traffic and looking for patterns based on very carefully constructed algorithms. If tripped, this service will start dropping that bad traffic before it even makes it into the network.
The second round is turned on when necessary and is powerful enough to inspect traffic for the more sophisticated SYN Flood attacks. Because an actual Network Admin powers the major portion of this process, the system can look into the types of SYN requests being made and decide if they’re good or bad. The bad requests are dropped and the attack is thwarted before it gets the chance to open that stale connection.
So I don’t have to worry?
Not necessarily. DDoS attacks are, at their center, a malicious attack. There’s no way to say exactly why an attacker targets a site and, like all crimes, there’s no way to ensure that you’re completely invulnerable. Luckily Liquid Web has you covered! Our always-on platform includes free mitigation of up to 2Gbps attacks, which is the bulk of the attacks we see. This protection is included with every server and server instance on our worldwide network, including our new Managed WordPress and Managed WooCommerce products. And, in the case of exceeding these levels, we can help!
Both of these mitigation functions are available to all our clients. If you have questions, please feel free to speak with one of our Heroic Sales professionals. They’ll be able to answer all your questions and setup mitigation service. You can also find more information here: https://fairmoon.net/dos-protraction/